Fill in your details!
We Provide All Kind Of Hacking Services For Your Desired Work :
Spouse Cheating
Mobile Monitoring
Credit Score Fix
Social Media Recovery/Access
Reputation Management
What we do?
We are the #1 Team of Professionals. make sure you know you're hiring the BEST!
- We're the only Certified company to hire online.
- We're the only Company online to Guarantee you will get results.
- You can back out any time before your project starts and get a full refund.
- 100% Confidential and we WON'T expose your confidential data to anyone.
SERVICES WE PROVIDE
You can hire our professionals for the various services like this :

Being Cyber Stalked
Hire a professional to help protect your children from cyber predators. Our professional can find the source and help close the case on any investigation. Hire our professional!
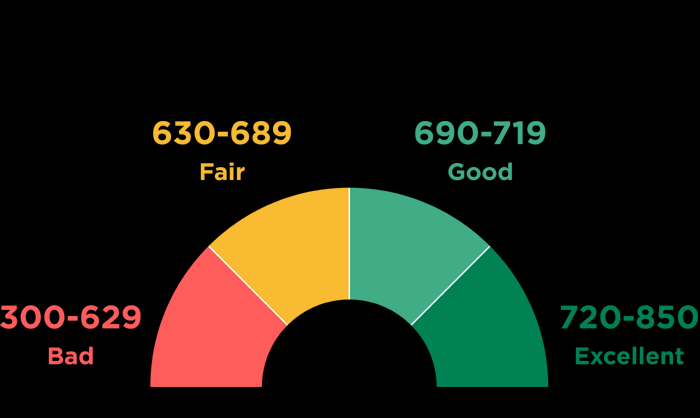
Credit Score Fix
Hire a professional to help you fix your bad credit score!

Spouse Cheating
Find out for sure what your spouse is up to with our Digital Investigation services. Hire a Professional!

Cryptocurrency Theft
Hire a professional to get your hard earned money back. Now a days many online crypto currency scams are scamming people.We can help you recover your money back.

Windows Desktop/Laptop/Macbook Hacked?
Hire a professional to recover/get access to a computer account for you. You present us with the Username and we will help you get the original password.

Location Finding Services
Find loved ones, missed connections or old friends with our world wide Person Locate Service. Hire a Professional!

News & Blog Articles
We can help you remove any kind of negative content posted against you, whether it's a blog or news article website.Just hire our professional.

Penetration testing
A penetration test is a simulated cyber attack against your computer system to check for exploitable vulnerabilities.It involve the attempted breaching of any number of application systems to uncover vulnerabilities.We can help you secure your web apps.

Blog Hacking
Hire a professional to recover/get access to a blog account for you. You present us with the details and we will help you get the access.Just hire our professional.
Software Access Help
We can help you get access to any software/app you want.Just hire our professional.

Website Hacking
Hire a professional to get access to a domain for you. You present us with the info and we will help you get the original password of admin panel.Just hire our professional.

Driving License Records
Are you facing difficulty with your driving license, we can help you erase your driving license records.Just hire our professional.
SOCIAL MEDIA ACCOUNT HACKING
You can hire our professionals for the various services like this :

Whatsapp Hacking
We can help you recover or get access to any whatsapp account you want.Just hire our professional.

Youtube Channel Hacking
We can help you recover or get access to any youtube account you want.Just hire our professional.

Instagram Hacking
We can help you recover or get access to any instagram account you want.Just hire our professional.

Snapchat Hacking
We can help you recover or get access to any snapchat account you want.Just hire our professional.

Facebook Hacking
We can help you recover or get access to any facebook account you want.Just hire our professional.

Skype Hacking
We can help you recover or get access to any skype account you want.Just hire our professional.
YOU CAN GET ACCESS TO THE FOLLOWING FEATURES :
Snapchat
Facebook Messenger
Location Tracking
Call Logs
Sms
Keylogger
FREQUENTLY ASKED QUESTIONS
HOW IT WORKS
Sign-up
Pay invoice
Track the task
Receive the result
Sending your message. Please wait...
Please complete all the fields in the form before sending.